Posted on 15 Dec 2022
In November, the UN’s Ad Hoc Committee released its first consolidated negotiating draft for a ‘cybercrime treaty’, to be discussed at the committee’s fourth session in Vienna in January 2023. Now that there is a draft, the real negotiations begin. But there is still a long way to go before the exact terms of the treaty are agreed upon.
The Ad Hoc Committee’s negotiating document for a convention on countering the use of ICT for criminal purposes is divided into three chapters: general provisions, criminalization, and procedural measures and law enforcement. Overall, the general provisions track closely with consensus that has coalesced during the 2022 meetings; the criminalization section leaves all decision-making to states, keeping almost all suggestions for now; the section on procedural measures and law enforcement offers wide cooperation on crimes outside the treaty, yet is thin on explicit protections or safeguards.
The text was developed from a combination of government submissions, which already borrowed heavily from the Council of Europe Cybercrime Convention (Budapest Convention) and the UN Convention against Transnational Organized Crime (UNTOC). The committee did not make any decisions on contentious terminology, leaving that to states to thrash out. In January, states will begin to make decisions based on the draft text. They are meant to observe consensus-based decision-making but can take decisions to a vote. To win a vote, however, requires a two-thirds majority of states present.
General provisions
The general provisions set out the purpose of the proposed convention, use of terms, scope of application, sovereignty and human rights clauses. Tracking closely with what the GI-TOC observed to be a developing consensus during the May–June 2022 meetings, the purpose of the convention includes combating and preventing crimes committed using ICT (‘cybercrimes’); promoting international cooperation; and technical assistance. The sharing of electronic evidence is not included under the treaty’s purpose, but rather noted in the scope of application. The inclusion of evidence collection under general provisions is significant because many countries see the collection of e-evidence as the main reason for a treaty.
Sovereignty clauses are taken from the UNTOC, a position shared among governments during the 2022 negotiations. This section currently does not deal with the thorny issue of cross-border data collection from third parties without government approval, which may be addressed in later chapters. The human rights section is likely to appear too weak for proponents of such clauses, as it does not list existing instruments, such as the International Covenant on Civil and Political Rights, which includes a right to privacy, and the Universal Declaration of Human Rights. There is a clause on gender mainstreaming and the needs of the vulnerable, which would elevate the relevance of these two issues across the treaty and provide a hook to include them under technical assistance. However, this current text would need to go further than this to ensure that safeguards are laid out across the treaty, to truly embed protections.
It is likely that an additional article will need to be included in this section, one that sets out this convention’s relationship to existing treaties, such as the Budapest Convention and the African Union Convention on Cyber Security and Personal Data Protection. There is little reference to the roles, rights and responsibilities of the private sector, an essential stakeholder for cybercrime, nor are there references yet to civil society as a stakeholder.
Criminalization
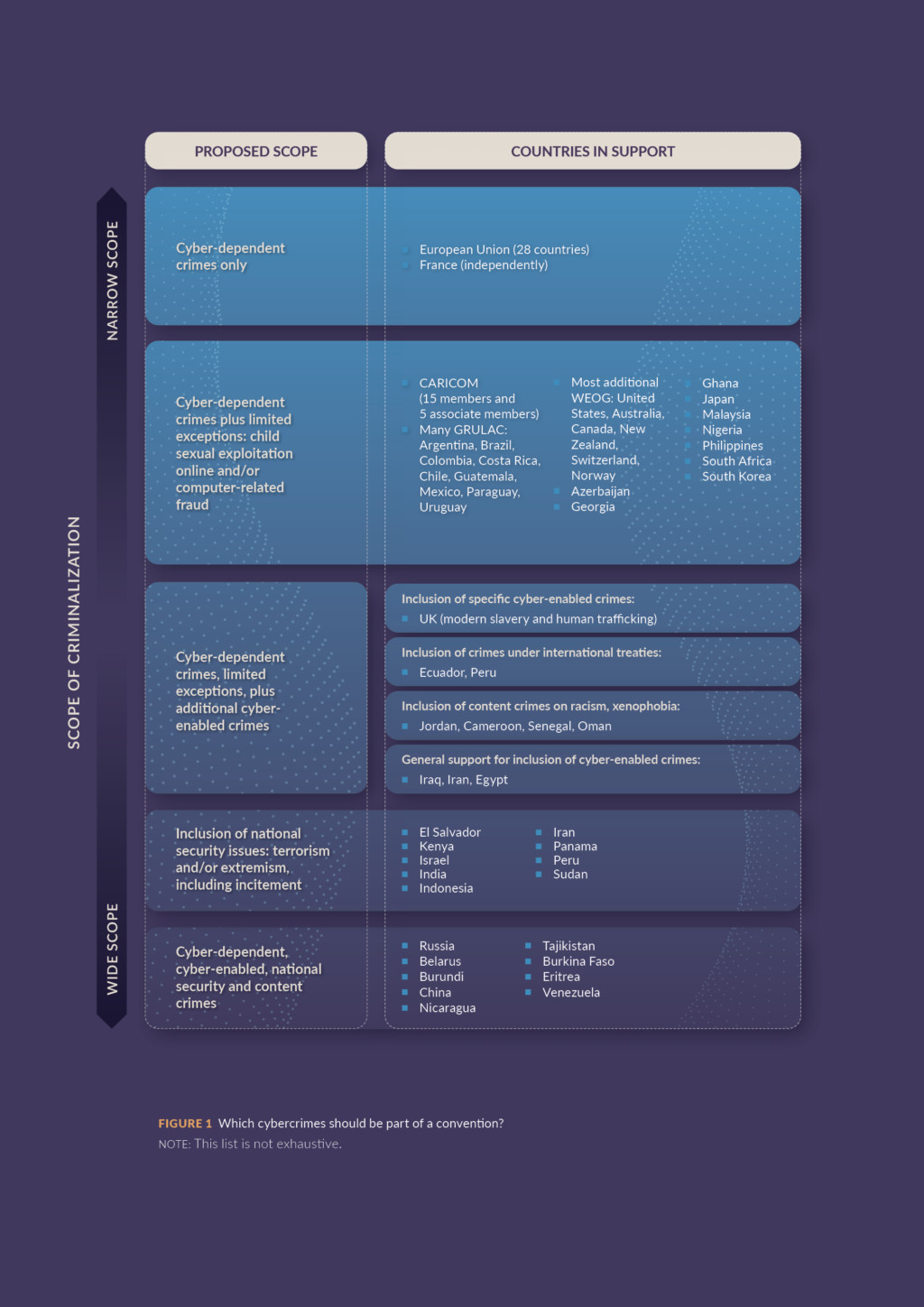
On criminalization, the committee has not made substantive decisions, but opted to include most suggestions by states, clustering them for discussion in January. In this way, they have put the decisions in the hands of government negotiators. Clusters 1–4 deal with cyber-dependent crimes (including fraud committed using ICT), which are not likely to be contentious. Many of these articles track with the Budapest Convention, with some alterations and additions. The committee has included options for aggravating circumstances to be applied in many cases.
The clusters then turn to cyber-enabled crimes, starting with provisions on criminalizing child sexual exploitation online and other forms of sexual exploitation online (e.g. non-consensual sharing of intimate images). The inclusion of many of these crimes has already received significant support from governments. However, there has been less support for additional categories such as incitement to suicide and cyberstalking. These clusters almost run as a protocol to a potential treaty, and are a significant step forward in terms of support for gender rights and children’s rights in a crime treaty – no country will want to look soft on these crimes. A potential concern is that its length could make rejection of later clusters seem unbalanced. However, negotiators have already voiced strong opinions on including further cyber-enabled crimes and are likely to stick to their positions.
Cluster eight focuses on incitement to political and social violence, including denial of genocides, which is Russia’s language and strongly opposed by Western countries. Given its isolated role at the UN following the invasion of Ukraine, Russia is unlikely to find a two-thirds majority vote if consensus cannot be achieved. Cluster nine is a grouping of terrorism, arms trafficking, drugs trafficking and illegal distribution of counterfeit medicines. There is unlikely to be consensus on these crimes, as they duplicate provisions in other treaties, and allowances are already made to cooperate on a wider set of crimes in later sections.
The odds are in favour of governments who want a limited scope of activities to be criminalized, as overwhelming support (two-thirds) has not been there for a more extensive list of cyber-enabled crimes.
Procedural measures and law enforcement
This section is wide-ranging on cooperation for criminal proceedings yet light on detail for safeguards to protect rights and privacy. On the technical measures, such as collection and preservation of traffic data, or interception of content data, the language nearly mirrors the Budapest Convention (which is also reflected in the Russia/China draft treaty). Additionally, the language on the protection of witnesses and victims has been taken from the UNTOC, as has the initial language on measures to enhance cooperation with law enforcement and jurisdiction.
The scope for cooperation is as comprehensive as possible, including cooperation on ‘other criminal offences committed by means of [a computer system] [an information, communication and technology system]’ (again, similar to the Budapest Convention and the Russia/China draft treaty). Although it replicates existing language, it is possible that this will permit unrestricted state cooperation across social, cultural and political spaces online, with potential negative consequences. A case in point is countries that criminalize sexual preference. Governments could plausibly request traffic data for dating apps frequented by LGBTQI individuals, and compel international companies to provide this data if the requesting and supplying country has complementary laws or agrees to cooperate.
The language on safeguards couches these within domestic laws with references to international law (also similar to the Budapest Convention and the Russia/China draft). The current draft does not list specific international instruments, but has added the need to incorporate ‘protection of privacy and personal data’ in addition to standard principles of proportionality, necessity and legality. So while it is less robust on outlining existing safeguards by naming treaties, it adds new areas of critical importance, such as protection of personal data.
As the GI-TOC has noted previously, if there is extensive flexibility afforded to procedural measures, what role will the chapter on criminalization play? For countries that seek a limited scope, a remaining challenge is how to make a treaty operationally useful while not creating an instrument that rubber-stamps oppressive state practices.
The road ahead
As the draft has been taken largely from government submissions, and these submissions, in turn, borrowed from existing instruments, a lot of the document’s language has a familiar ring. Criminalization is likely to be the chapter where the hardest lines are drawn and the debate is most heated. Yet, this effort should be complemented by introducing measures – on issues such as rights, safeguards and protections – into subsequent chapters that shape the treaty using the same principles. With this first negotiating text, the chair has fired the starting gun on the real negotiations, but negotiators have a long and arduous road ahead of them before the ink dries on the paper.



