Posted on 04 Apr 2024
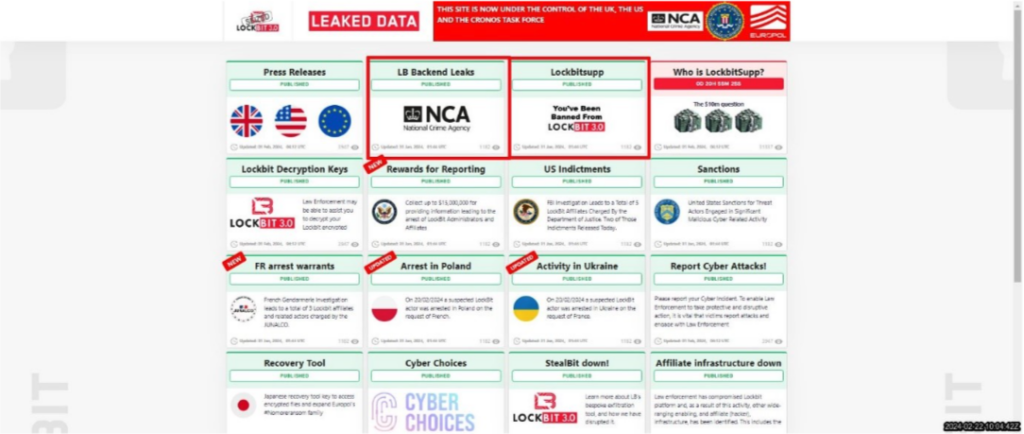
On 20 February 2024, the UK’s National Crime Agency (NCA) posted a series of tweets in the style of a countdown clock before releasing a video revealing that it had taken control of the entire infrastructure of the world’s largest and most prolific ransomware-as-a-service (RaaS) provider, LockBit. This was part of Operation Cronos, an international task force involving law enforcement agencies from a number of countries.
Alongside the infrastructure takedown, more than 200 cryptocurrency accounts were frozen, sanctions were imposed, 34 servers and 14 000 accounts were taken down, and three LockBit affiliates were arrested in Poland and Ukraine. It was also discovered that although the site had promised to delete victims’ exfiltrated data once the ransom had been paid, this had not been done.
When other RaaS sites have been taken down, they have simply gone offline or a law enforcement seizure notice has appeared where the site used to be. However, the February 2024 takedown stands out because the LockBit site itself was repurposed by law enforcement – including for press releases, decryption keys, news of affiliates’ arrests and indictments. Law enforcement had succeeded in ‘trolling’ one of the world’s most prominent cybercriminal enterprises.
The move was widely applauded across the cybersecurity community. Law enforcement even released a list of the site’s affiliate usernames because, as the NCA’s video of the takedown warns: ‘We know who they are, and we will be watching.’
What is LockBit?
LockBit is a RaaS provider, meaning it provides the platform, infrastructure and tools for other threat actors or individual affiliates to carry out ransomware attacks. It rose to prominence after the Conti ransomware group disbanded in 2022, attracting affiliates, including notorious threat actors such as FIN7 and Evil Corp, as well as former Conti members, to its service. According to threat intelligence firm PRODAFT, LockBit appears to have developed a bespoke version of the software for these former Conti members, known as LockBit Green.
Operating like a business, LockBit launched promotional campaigns, such as paying US$1 000 to those willing to have the LockBit logo tattooed somewhere on their body. Like other tech companies, it launched a bug bounty programme, encouraging hackers to search for and report vulnerabilities in the source code. The platform itself was highly customizable and easy to use.
But what really set LockBit apart from other RaaS providers was its payment model. Typically, RaaS providers would receive the entire ransom payment from the victim and then pay the majority to the affiliate, taking a percentage. LockBit allowed affiliates to collect the ransom payment themselves and then took its 20 per cent cut.
According to Cisco Talos Intelligence Group, LockBit was responsible for 25 per cent of global ransomware deployments in 2023. But LockBitSupp, LockBit’s leader, also has an interesting reputation in the cybercriminal landscape, having been banned from the two most prominent Russian-language underground forums, XSS and Exploit, for allegedly failing to pay an initial access broker. In 2022, LockBitSupp had a dispute over paying a bug bounty with the developer of LockBit 3.0, the latest version of the software, which resulted in the source code being leaked by the developer.
How did it respond?
Since the takedown, LockBit has quickly resurfaced. A new site was up and running within a week. But eagle-eyed security researchers noticed that some of the ransom victims posted had been recycled.
What followed was a lengthy statement from LockBit sent to cybersecurity website Vx-underground, in which LockBit underplayed the significance of the breach and blamed ‘negligence and irresponsibility’, having become ‘very lazy’ after five years of ‘swimming in money’.
In the world of cybercrime, trust is your reputation – as the recent ALPHV/BlackCat exit scam shows. Whether LockBit’s response is effective remains to be seen. It was such a public takedown that it certainly caused irreparable damage. The question is, how much?
What this means for the future of RaaS is hard to say. LockBit is not the only RaaS provider – Black Basta or Rhysida are among the others – although it is by far the largest. But affiliates will often use multiple RaaS providers at the same time.
Another development is the growth of so-called ‘closed groups’, such as Royal ransomware (believed to have been formerly part of Conti) and Play ransomware, which are much harder for law enforcement to penetrate, as they are kept private.
Interviews by the GI-TOC with threat intelligence experts suggest that the future lies in the value of exfiltrated data, and that new marketplaces for data brokerage will emerge. But for now, with the average ransom payment at US$1.5 million, there is clearly still a lot of profit to be made from ransomware. Until victims stop paying, the business model will remain strong and the game of whack-a-mole between law enforcement and cybercriminals will continue.
LockBit, the world's largest ransomware-as-a-service (RaaS) provider suffered a very public takedown by an international law enforcement task force, Operation Cronos.
The ransomware behemoth quickly relaunched just days later. But in a world where trust is key, might the reputational damage be too great?
This is the story of the rise of LockBit, its relationship with other infamous cybercriminal groups, its uneasy relationship with some affiliates, its curious leader LockBitsupp, the public takedown and the relaunch, and what this means for the future of ransomware-as-a-service.
Speaker(s):
Koryak Uzan, Co-founder & Managing Director of PRODAFT
Links:
GITOC - The Rise and Fall of the Conti ransomware group
PRODAFT - LockBit: Behind the Lines of the Notorious RaaS
PRODAFT - The Demise of LOCKBIT: Disrupting the Most Prominent Ransomware Gang by Utilizing Upstream Threat Intelligence
https://twitter.com/PRODAFT
https://www.trendmicro.com/vinfo/gb/security/news/ransomware-by-the-numbers/lockbit-blackcat-and-clop-prevail-as-top-raas-groups-for-1h-2023
https://www.wired.com/story/lockbit-ransomware-takedown-website-nca-fbi/
https://krebsonsecurity.com/2024/02/fulton-county-security-experts-call-lockbits-bluff/
https://www.blackfog.com/the-top-10-ransomware-groups-of-2023/
https://go.recordedfuture.com/webinar/threat-briefing/lockbit-takedown
https://www.bloomberg.com/news/articles/2024-02-19/fbi-uk-crime-agency-say-they-have-disrupted-lockbit-hacking-gang?cmpid=cyber
https://www.bleepingcomputer.com/news/security/lockbit-ransomware-returns-to-attacks-with-new-encryptors-servers/
https://www.nationalcrimeagency.gov.uk/news/nca-leads-international-investigation-targeting-worlds-most-harmful-ransomware-group
https://samples.vx-underground.org/tmp/Lockbit_Statement_2024-02-24.txt
https://therecord.media/lockbit-lied-about-deleting-exfiltrated-data-after-ransom-payments
https://www.sophos.com/en-us/content/state-of-ransomware
https://www.trendmicro.com/vinfo/gb/security/news/ransomware-spotlight/ransomware-spotlight-rhysida
https://www.theguardian.com/commentisfree/2024/feb/06/hacker-british-library-cybersecurity-cybercrime-uk
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-352a
https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-royal
https://www.reuters.com/technology/cybersecurity/blackcat-ransomware-site-claims-it-was-seized-uk-law-enforcement-denies-being-2024-03-05/
https://thehackernews.com/2024/03/exit-scam-blackcat-ransomware-group.html
https://twitter.com/ddd1ms/status/1764979901965201552
https://www.cpomagazine.com/cyber-security/under-increasing-federal-scrutiny-blackcat-ransomware-gang-pulls-exit-scam-on-its-way-out/
https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/resurgence-of-blackcat-ransomware/
https://www.cpomagazine.com/cyber-security/blackcat-ransomware-gang-recovers-from-early-december-law-enforcement-operation-restores-websites-seized-by-doj/
https://www.darkreading.com/threat-intelligence/lockbit-leak-site-reemerges-week-after-complete-compromise-
https://www.linkedin.com/posts/prodaft_manual-ransomware-business-activity-7026870344648916992-mgZX/?originalSubdomain=nl
https://therecord.media/lockbit-ransomware-indictments-us-doj-bassterlord
https://home.treasury.gov/news/press-releases/jy2114
https://therecord.media/lockbit-affiliates-arrested-in-ukraine-poland
https://www.reuters.com/technology/cybersecurity/ukraine-arrests-father-son-duo-lockbit-cybercrime-bust-2024-02-21/
https://www.chainalysis.com/blog/lockbit-takedown-sanctions-february-2024/
https://www.europol.europa.eu/media-press/newsroom/news/law-enforcement-disrupt-worlds-biggest-ransomware-operation
https://analyst1.com/this-forum-is-a-bunch-of-communists-and-they-set-me-up-lockbit-spills-the-tea-regarding-their-recent-ban-on-russian-speaking-forums/
https://securityaffairs.com/149941/hacking/lockbit-3-leaked-code-usage.html
https://www.bankinfosecurity.com/ransomware-as-a-service-gang-lockbit-pays-first-50k-bounty-a-20099
https://therecord.media/wazawaka-cyber-most-wanted-interview-click-here
https://www.state.gov/the-department-of-state-announces-reward-offer-against-russian-ransomware-actor/
https://www.fbi.gov/wanted/cyber/mikhail-pavlovich-matveev
https://www.bleepingcomputer.com/news/security/evil-corp-switches-to-lockbit-ransomware-to-evade-sanctions/
https://resources.prodaft.com/fin7-cybercrime-gang
https://analyst1.com/ransomware-diaries-volume-1/
https://www.mimecast.com/content/darkside-ransomware/
https://www.cisa.gov/news-events/cybersecurity-advisories/aa21-291a
https://www.bleepingcomputer.com/news/security/lockbit-ransomware-goes-green-uses-new-conti-based-encryptor/
https://blog.talosintelligence.com/ransomware-affiliate-model/
https://www.csoonline.com/article/573937/with-conti-gone-lockbit-takes-lead-of-the-ransomware-threat-landscape.html
https://youtu.be/0EQenbbPSaE
https://threatpost.com/darkside-hackers-court-paying-affiliates/166393/
https://www.nytimes.com/2021/05/13/us/politics/biden-colonial-pipeline-ransomware.html
https://twitter.com/vxunderground/status/1568273779050127363?lang=en
https://twitter.com/vxunderground/status/1568981950043414530?lang=en
https://www.microsoft.com/en-us/msrc/bounty
https://bughunters.google.com/
https://www.bleepingcomputer.com/news/security/lockbit-30-introduces-the-first-ransomware-bug-bounty-program/
https://analyst1.com/lockbit-takedown-operation-cronos-a-long-awaited-psyops-against-ransomware/
https://twitter.com/vxunderground/status/1697027546452259277
https://twitter.com/NCA_UK/status/1759888184979157123
https://twitter.com/NCA_UK/status/1759873080069910955
https://twitter.com/NCA_UK/status/1759857979086499939
https://www.europol.europa.eu/media-press/newsroom/news/law-enforcement-disrupt-worlds-biggest-ransomware-operation
https://www.justice.gov/opa/pr/us-and-uk-disrupt-lockbit-ransomware-variant
https://twitter.com/NCA_UK/status/1759842879688655053
https://twitter.com/NCA_UK/status/1759906806044725514
https://therecord.media/an-interview-with-lockbit-the-risk-of-being-hacked-ourselves-is-always-present



